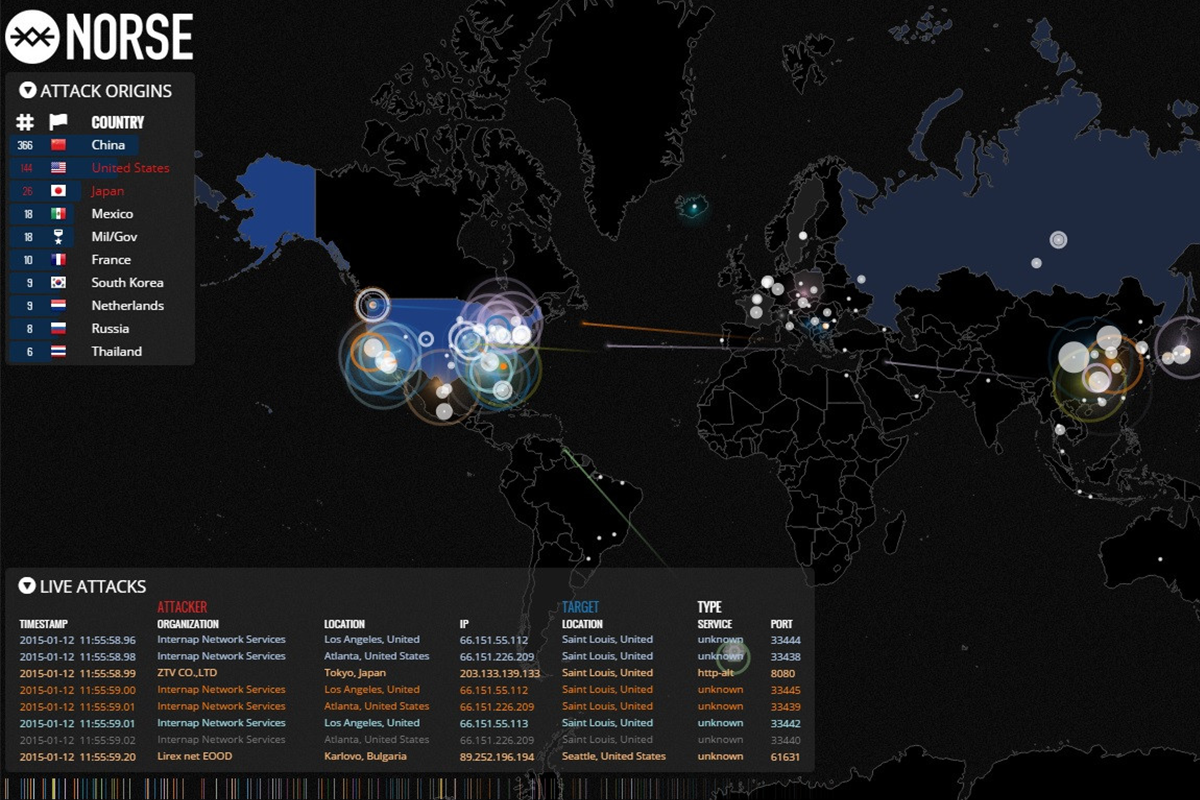
Every day, it seems like there’s a report of a new data breach at a major company. This live map showing attempted hacks on just ONE honeypot server is sobering. Even if you’re not a huge corporation, your data is still one of your company’s most valuable assets. Preventing digital theft of intellectual property, trade secrets, or confidential information is critical. The problem is that even if your in-house network is secure, your employees likely are using mobile devices that represent opportunities for security breaches.
Microsoft Windows still represents the most used operating system, but it’s nowhere near the 95% market share it enjoyed in the past. In fact, PCs themselves are being overtaken by an array of smartphones, tablets, and personal devices that are constantly requesting access to your network from different locations and at different times. Users are too busy worrying about their day-to-day job duties to concern themselves with security policies, even if they are tech-savvy enough to stay away from malware, phishing schemes, and other infiltration by bad actors.
Because so many of these devices are not available to scan during off-peak times—or at all—a traditional network security scan is ineffective. These unscanned devices and the unencrypted data they harbor are the “dark matter” of your network. They exist, and they’re important to the function of your company… but there’s no way to quantify the risk they pose with traditional vulnerability scanning.
Scanning Your Complete Network for Vulnerabilities—24×7
iScan Online is a newly patented technology that addresses the problem of “dark matter.” It uses “Opportunistic Scanning” to perform assessments on devices accessing network resources when AND where they are available. By being flexible, devices can be assessed regardless of their network connection or location—as long as they are connected to the Internet. iScan Online is deployed through a browser plugin, as a standalone application for your desktop computers, or as a native mobile app. It’s fast, highly accurate, and leverages the technology you already have in place: Microsoft Active Directory, Systems Management tools, Web Applications, Internet access, and a browser.
The way that iScan Online performs is both highly accurate and unique in the market. An integrated web portal provides a single point for management, analysis, and reporting, while the individual devices perform the heavy lifting of the scan process. Whether you need dozens, hundreds, or thousands of devices scanned, this distributed architecture allows them to be scanned in a matter of seconds. Best of all, there is no lengthy deployment cycle or additional network appliance to purchase.
Identifying Unprotected Data
iScan Online’s Data Discovery Scan identifies what devices store unprotected trade secrets, intellectual property, and personal identifiable information that are putting your business at risk. With iScan Online, you can see every unprotected piece of data within your company, from credit cards and Social Security numbers in Dropbox, to intellectual property in mail folders and .ZIP files. This comprehensive data discovery and scanning solution meets or exceeds today’s regulatory requirements at the federal, state, and industry level. This is particularly important for organizations with regulatory compliance mandates like those from the PCI Council or HIPAA. iScan Online can be configured to run various types of scans required to demonstrate compliance with regulations.
Analytics for Potential Security Breaches
One of the best parts about iScan Online is that it aggregates its raw scan data into an aesthetically pleasing, actionable console. The console can be organized by role and report focus, and the reports are designed to work in concert to allow full awareness of exposed data, vulnerable devices, and financial liability. You can immediately see your highest priorities. And if you work with I.T. Roadmap, we can demonstrate the ROI over time as we proactively remediate your security threats and track reduction in financial exposure.
If you’re interested in a data security solution that doesn’t require the purchase of new equipment, doesn’t increase your network load, and proactively ensures that all devices connected to your network are scanned for vulnerabilities, contact I.T. Roadmap to implement iScan for you today.